 Sauron is the first artificial Ethical Hacker, to protect individual devices or entire network infrastructures, capable of identifying suspicious connections, analyzing their behavior, and creating a report “on the intention” of the software or remote computer,
Sauron is the first artificial Ethical Hacker, to protect individual devices or entire network infrastructures, capable of identifying suspicious connections, analyzing their behavior, and creating a report “on the intention” of the software or remote computer,
in order to identify and block malware, hacker attacks, and data theft.
Compared to the competitors (e.g. EDR, XDR, SIEM), Sauron doesn’t need predefined rules but learns autonomously how to recognize and block an attack or a 0-days malware directly from expert SOC operators, providing them all necessary tools to make a Deep Analysis of the network, in order to contextualize his movements and learn from the controls and actions they performs, without having to necessarily instruct the learning engine, but favoring learning through emulation. Compared to the reference market and the software offered by competitors, Sauron presents many advantages:

- It autonomously analyzes the low-level behavior of processes and threads for each active network connection
- Performs detailed analysis of the client by associating a level of reliability to the Mc-Address based on the behavioral parameters of its user
- If it identifies an “enemy”, it propagates the identikit to all the network infrastructures protected by Sauron, to block the mac addresses identified everywhere
- Learn from the best: Sauron learns how to identify suspicious behavior from professional Ethical Hackers without having to learn difficult AI Learning procedures, Sauron learns independently
- It integrates a powerful NLP engine for learning and autonomous analysis of the Language
- It recognizes frie
- nds as enemies by not allowing them to obtain information or carry out any other operation on protected infrastructures
- It is a powerful tool but very easy to use
Sauron is intelligent and methodical – A paradigm shift supported by the most modern Artificial Intelligence development techniques: Sauron not only analyzes the behavior of the threads and the exchanged packets, but also any type of client (Mobile OS or PC Desktop) that attempts access to the protected network, to trace a “psychological profile of the device”.

Sauron Intelligence: The Synthetic Psyche
The Synthetic Psyche methodology studies the human mental processes behavior, with the aim of replicating them in intelligent software acting independently from the context and nature of the data.
The Synthetic Psyche is a group of AI algorithms whose main objective is not limited to understanding the human brain functions, but rather include the study of how the human cognitive processes work, with the objective to emulate them.
One of the most important principles of this approach is that, with the Syntetic Psyche, we simulate each cognitive process involved in all cases that require both intelligence and experience.
By simulating our cognitive processes, it isn’t necessary to develop a Neural Network for each function.
The Synthetic Psyche approach, is much more complex than the classical approach, as it implies a deep knowledge of the functional processes of the human mind.

Stress Test and Results
Below are the types of attacks carried out by Ethical Hackers in order to instruct the Sauron database to be populated with multiple types of attacks and help the algorithm learn to recognize similar malicious activities in the future. The methodology used to achieve the goal is based on OWASP Top 10, various Common Vulnerabilities and Exposures (CVE) and Chinese National Vulnerability Database (CNNVD).

Sauron – A Synthetic Eye for your Security
Sauron includes two types of Dashboards, one for deep monitoring of the network and one that contains detailed statistics on attacks in progress and those rejected

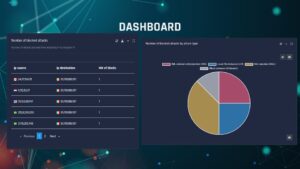
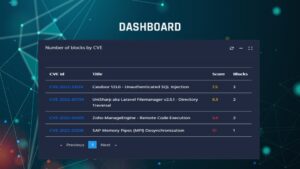
Sauron: the most advanced Self-Learning system ever created
Sauron for Mobile and IoT Devices
In most attacks, professional hackers make use of tools such as to use clients as “trojan horses” to penetrate an IT infrastructure. With Sauron it is possible to protect not only the servers but all the clients that connect to one or more networks from most of the known attacks:
- Banking Malware:Theft of bank data
- Mobile Ransomware: Block access to user data, such as documents, photos, and videos
- Mobile spyware: user activity monitoring
- Financial Attacks: Cyber attacks on financial services
- MMS Malware: Viruses sent via SMS
- Mobile Adware: Viruses designed to deliver advertisements to the user
- SMS Trojan – Trojans sent via SMS

Overlay Malware: malicious application, superimposing itself on the legitimate one or emulating clicks on windows, buttons, and menus, may be able to perform actions on behalf of the unsuspecting victim, stealing any data entered such as passwords, codes, and PINs and subsequently forwarding them to a central remote and manned command.
Sauron analyzes and validates each packet exchanged, incoming and outgoing both from the network and from the single-end Device. The interaction with the most advanced Natural Language Processing systems makes it useful for the contextualization of the data to carry out forecast calculations and analyses on the basis of multiple forms of data.
